articles
China Elevator Stories
Repeated Security Breaches by a hacker
I have experienced repeated security breaches.
03/06/2024

Ruth Silbermayr
Author
I am experiencing being hacked almost daily.
The first time I realized a man had hacked into my computer was when a second mouse appeared on my screen while I was editing pictures.
Only a few days before this happened, he had asked me to download a program that would allow me to search for spyware on my computer. This was not software to protect my computer, but spyware disguised as anti-spyware software that enabled him to hack into my computer instead.
He would stop me from editing pictures, watch everything I did on my screen live on his screen, freeze my screen while I was working so I could not finish projects, hack into my blog, change titles, change photos, and more.
Once I realized this, I uninstalled the software, but it turned out that uninstalling it made no difference. Ever heard of a program that would not let you uninstall it once installed? I haven’t, but I do believe that this is what happened. Another scenario could have been that he installed another program remotely before I uninstalled the software, allowing him to stay in my computer.
In my experience, the problem with spyware installed by another person is that it is commonly invisible and therefore hard to detect or cannot be detected at all.
When I logged into my blog one day, I found my profile picture had been repeatedly uploaded. A hacker had also changed my picture on quite a few of my pages. I tried to change them all back to one single profile picture but found that this was taking up way too much time, particularly because he simply uploaded new pictures and changed them whenever I was working on changing them back.
I eventually gave up and left it at that.
Another time I encountered a problem with hacking was when I was looking for a job. During that time, I used my personal website as an online portfolio I could send with my job applications.
Right before I had a job interview, my website and my blog both went completely empty. They had been hacked, and somebody had installed a virus on both pages. I resolved the issue with the help of my hosting provider for my blog, but I wasn’t able to fix the issue on my personal website.
My provider told me they were not familiar with this issue, did not know how to fix it, and that this was the first time they had encountered this specific problem.
Another occurrence where I realized someone had changed private information was when I went to a pharmacy to get prescription iron supplements. Even though my income was low enough that I would not have had to pay a prescription fee, when I asked the employee for the supplements, their system showed that I had to pay a fee.
Upon encountering this problem, I contacted my health insurance company, because this is where pharmacies get their information from. But when I called them, they said their system showed that I didn’t have to pay a prescription fee. They issued me a letter stating this so I could show it to the pharmacy.
When I went back to the pharmacy, their system still showed that I had to pay a fee. Even though I had a letter showing I did not have to pay a prescription fee, I could not solve this problem with the pharmacy (the information can only be changed through the health insurance company, which told me it had the correct information – the pharmacy’s system, on the other hand, displayed the wrong information). The problem could only be resolved once the hacker hacked into whichever place he had hacked into to change my information back to the original data.
Because all of the data was in German, I believe it was not my ex-husband who hacked into their system. I also do not know that my ex-husband would have such advanced hacking skills, but I do know that this particular person has advanced hacking skills.
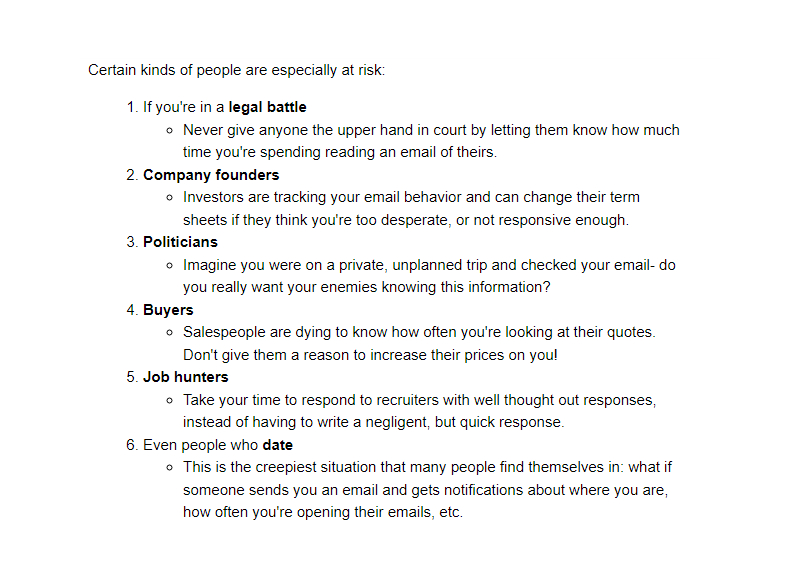
He has also been hacking into other people’s accounts, and I have received weird emails from these accounts, such as the email (excerpt) shown in the picture above.
After my email accounts had been hacked multiple times, I chose one company to transfer all my emails to two new email accounts. I signed up to receive their newsletters, and voilà, this is an email I recently received.
As far as I can discern, the email in the picture above was written by this particular stalker and is not from this company – it looks professional enough, which can make it hard to distinguish from an email written by an employee of this company.
I have had this happen not only once but many times by now, so I am aware that this can happen!
I also believe that this has to happen repeatedly until a person can grasp what is actually going on.
Let’s say this only happened twice, and I was not aware that I was being stalked and hacked – I probably wouldn’t know it could be a stalker. But let’s say this happens all the time and the other person has given me enough clues – I would then have enough experience to know that this may actually be a hacker.
This person has also appeared under various names on whichever platform I am on, writing to me disguised as someone else. Believe me, you will eventually become (almost) paranoid if you don’t know whether people writing to you are real or if this is a stalker disguised as another person or a hacker who has accessed another person’s account.
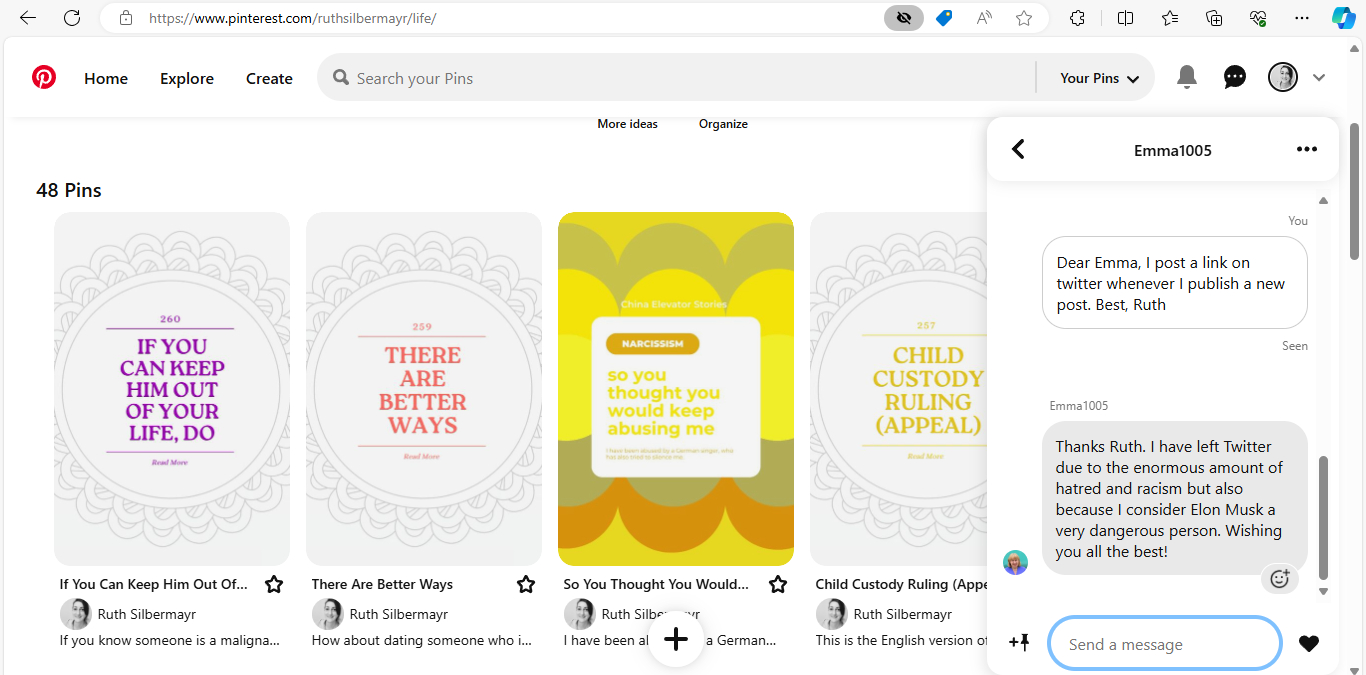
He will usually give himself away somehow, but sometimes it can be hard to know, such as in this message I received on Pinterest. In the last message, the person wrote she was not on Twitter anymore, which could point to this person, who stopped using Twitter years ago.
I am familiar with his writing style by now, but let me tell you, this is crazymaking behavior (also known as gaslighting)!
For example, he likes to put information into names. Em-ma: Emil’s ma, 1005 – I haven’t been with my older son, Emil, from the ages of 5 to almost 10.
Some of the accounts look real enough, so I do not know if he created an account that looked real, found this person, then logged into her account, or found an account and changed the name when he contacted me.
If you encounter such a situation once, it is no big deal! But imagine encountering these problems frequently, sometimes daily, almost anywhere you go, and with whomever you come in contact.
Have you ever been hacked?